Let’s get to know Encrypted Client Hello (ECH), a revolutionary TLS 1.3 protocol extension that facilitates the encryption of the whole Client Hello message. Sent during the preliminary stage of TLS 1.3 negotiation, ECH secures the payload using a public key that the web browser, known as the relying party, must know beforehand. This encryption method is most useful for large Content Delivery Networks (CDNs) that browser vendors are already familiar with.
ECH originated as Encrypted Server Name Indication (ESNI), an experimental extension introduced in 2018 to mitigate the risk of domain eavesdropping. As ESNI evolved into ECH, more comprehensive encryption was implemented, encompassing the entire Client Hello instead of only the Server Name Indication (SNI).
In practical terms, ECH represents a substantial leap in privacy protection. When a user visits an ECH-enabled website on Cloudflare, only the user, Cloudflare, and the website owner can identify the website visited.
Limitations of Transport Layer Security (TLS)
Although SSL and TLS protocols have been instrumental in preventing eavesdropping and ensuring the confidentiality and integrity of web content, they come with limitations. For example, while the actual content of a webpage is encrypted and protected, it’s still possible for intermediaries to infer a user’s activities through methods like analyzing the DNS request or the Server Name Indication (SNI).
Let’s consider the scenario where an IP address hosts multiple websites, a common occurrence with services like Cloudflare or other denial-of-service attack protection. The Server Name Indication becomes a privacy vulnerability, as shown in the following steps:
- Use
tsharkto capture packets from a specific IP address:tshark -w /tmp/pg.pcap port 443 and host <IP_ADDR> - Visit a website.
- Stop the packet capture after visiting the website with CTRL + C.
- Analyze the results:
wireshark -r /tmp/pg.pcap. You’ll see the TLS handshake for the Privacy Guides website. Around frame 5, look for "Client Hello". - The SNI value, which discloses the visited website, can be extracted with the
tsharkcommand:tshark -r /tmp/pg.pcap -Tfields -Y tls.handshake.extensions_server_name -e tls.handshake.extensions_server_name.
Despite the use of encrypted DNS servers, the SNI likely reveals the visited domain. This issue is set to be nullified by the introduction of ECH, which encrypts the entire Client Hello, preventing information leakage.
Cloudflare released Wireshark traces that demonstrate the difference between a normal TLS handshake and one that includes the ECH extension. As can be seen from the traces, the server name is revealed in the normal TLS handshake, but it is hidden when the ECH extension is used. This demonstration highlights the significant privacy improvements brought about by ECH.
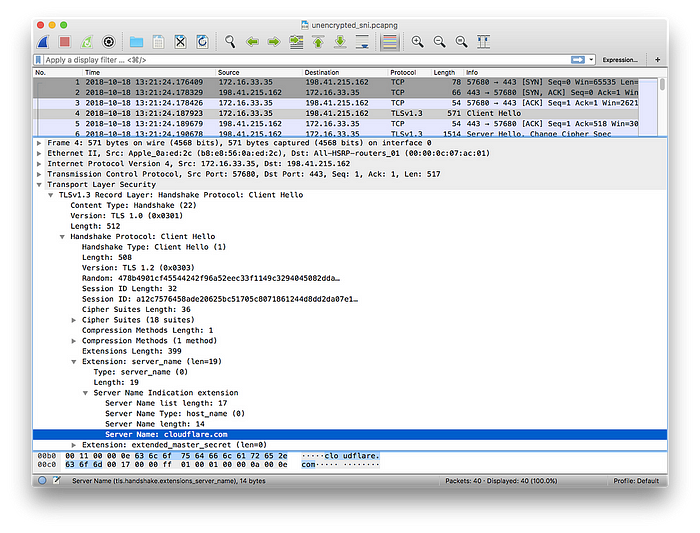
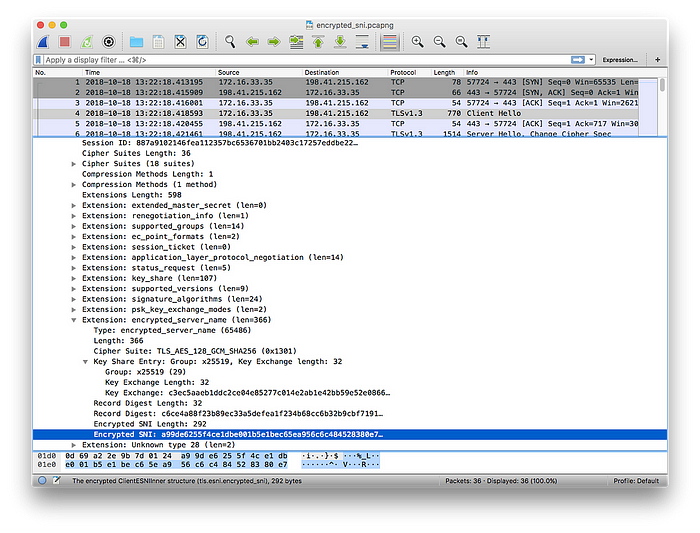
It’s important to note that countries like China and Russia are already blocking, or have expressed intentions to block, the use of ECH.
Exploring the Mechanism of ECH
ECH is designed to enhance the privacy of the TLS handshake, which starts with a ClientHello part. This message contains information about the ciphers to use, the TLS version, and most importantly, the server the client is trying to access (SNI).
Here’s how ECH works: The ClientHello message is split into two sections—an inner part and an outer part. The outer part carries non-sensitive details, while the inner part, encrypted, carries the "inner SNI".
The "outer SNI" is a common identifier signifying that a user is attempting to visit an encrypted website on Cloudflare. The "inner SNI" contains the actual server name the user intends to visit. This data is encrypted using a public key and can only be read by Cloudflare. Once the handshake is complete, the webpage is loaded as normal, just like any other TLS-protected site.
In the example below, a user is visiting example.com. Without ECH, any intermediate networks will be able to detect the website being accessed by the user. With ECH, the visible information will be limited to cloudflare-ech.com instead.
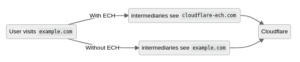
The Ultimate Aim of ECH
The main goal of ECH is to ensure indistinguishability of TLS connections to different origin servers behind the same ECH service provider. This means that when connecting to an origin behind Cloudflare, no one on the network between you and Cloudflare should be able to determine the origin you reached, or which handshake parameters you negotiated.
Besides providing immediate privacy, ECH policy, if fully achieved, can pave the way for the deployment of new features for TLS without compromising privacy. This is crucial as there is a risk of information leakage through traffic analysis, a method to understand the communication channel properties without decoding the underlying encryption scheme. Current ECH specifications provide some mitigations, but their coverage is incomplete, making ECH’s resistance to traffic analysis an area that warrants future exploration.
How to Enable ECH for Websites Behind Cloudflare
To enable ECH for your websites on Cloudflare:
- Log in to the Cloudflare dashboard
- Select your account and domain
- Go to SSL > Edge Certificates
- Enable Encrypted ClientHello (ECH)
Enabling ECH on Browsers
Firefox
ECH is now supported at Cloudflare DNS service and in Firefox. Follow these steps:
- In Firefox, go to: Settings > General > Network Settings > Enable DNS over HTTPS and choose Cloudflare as the provider
- In the about:config page, search for the echconfig and enable it
Chrome or Brave Browser
To enable ECH on your Chrome or Brave browser, follow these steps:
- Navigate to:
chrome://flags/#encrypted-client-hello - Enable the Encrypted ClientHello flag
- Restart Google Chrome
To verify your browser’s ECH status, visit https://defo.ie/ech-check.php
ECH Adoption in 2023
ECH has recently gained considerable traction. In July 2023, the IETF117 meeting revealed that Chrome and Firefox were undertaking a 1% sample trial of ECH. The final draft of ECH is expected to be submitted to the IESG for evaluation by January 2024.
Governments have already started taking measures in response to ECH. The Great Firewall of China began blocking ESNI traffic in August 2020 while still allowing ECH traffic. Around the same time, Russian ISP Rostelecom and its mobile operator Tele2 also began blocking ESNI traffic.
Cloudflare started supporting ECH for hosted domains in September 2023. Following this, Mozilla enabled ECH by default in Firefox v118 in October 2023.
Conclusion
In conclusion, ECH represents a significant stride forward in ensuring user privacy without compromising the efficiency and function of web services.
As privacy becomes increasingly important in our digital age, the continuous development and improvement of protocols like ECH are a fundamental necessity.
How Alstra Can Help
At Alstra Solutions, we prioritize the privacy and security of our clients. Our dedicated team of experts is ready to help your organization adapt and implement Encrypted Client Hello (ECH).
We will guide you through each step, from enabling ECH for your websites on Cloudflare to optimizing ECH settings across all browsers used within your organization. As a successful part of the wider technological community, we stay at the forefront of all developments, ensuring that your business benefits from the latest advancements, such as ECH.
Trust in Alstra Solutions to provide privacy-focused web solutions that enhance your security and help maintain your customers’ trust.

